Check out a real Cyber Security Plan
04 Nov 2022 - Justin Higgins
One of the most important things we do with our clients is to produce a Cyber Security Plan. This plan contains all of the personlized recommendations we make for you and customer and documents the technical information and details of your situation. As part of our support services we continuously update the plan as new technical and security information arises.
Since most people haven't seen a cyber security plan we have published an example plan so you can see what you'll get from IRL Cyber and how it help you stay secure and gain confidence you can use your devices without jeopardizing your security.
The Plan
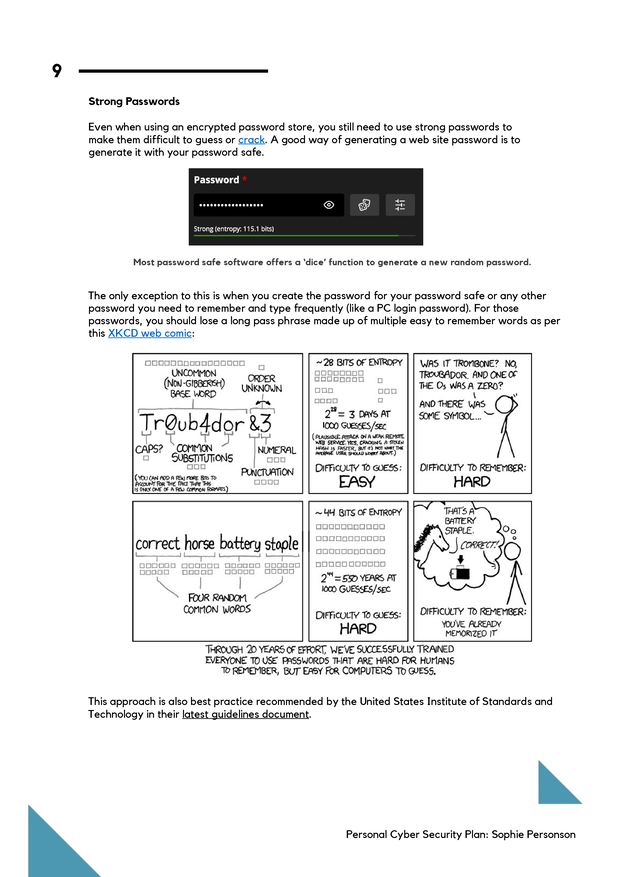
When we develop your plan, we work mith you to answer five questions as per the EFF's surveillance self defense guide:
- What do I want to protect?
- Who do I want to protect it from?
- How bad are the consequences if I fail?
- How likely is it that I will need to protect it?
- How much trouble am I willing to go through to try to prevent potential consequences?
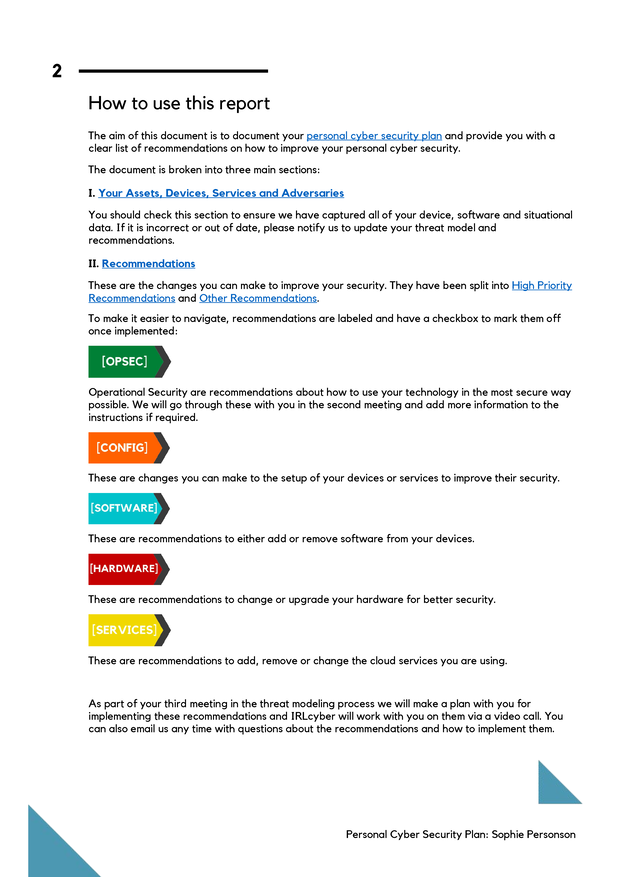
- [OPSEC] - Operational Security are recommendations about how to use your technology in the most secure way.
- [CONFIG] - These are changes you can make to the setup of your devices or services to improve their security.
- [SOFTWARE] - Recommendations to either add or remove software from your devices.
- [HARDWARE] - These are recommendations to change or upgrade your hardware for better security.
- [SERVICES] - Recommendations to add, remove or change the cloud services you are using.
All of these categories are clearly tagged within the document so you can concentrate on making the type of changes that suit you right now.
The recommendations are different for everybody, because we write them specifically to cater for your devices, services, needs and situation.
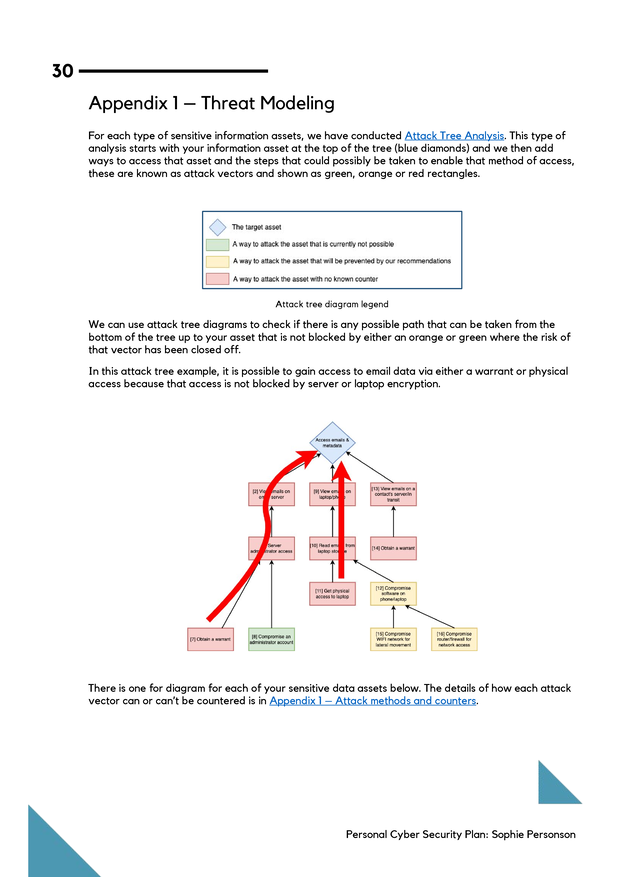
We generate these recommendations by researching how your devices and services work, checking to see what known vulnerabilities have been published and building a threat model. All of this information, including threat model diagrams and explanations are included in the document appendixes.
You don't have to read these yourself, but you'll have that information avilable for reference or to pass onto any technical people you work with in the future.
If you have any questions about anything in the plan, how it works or how it might apply to your situation, please don't hesitate to contact us and start a conversation.